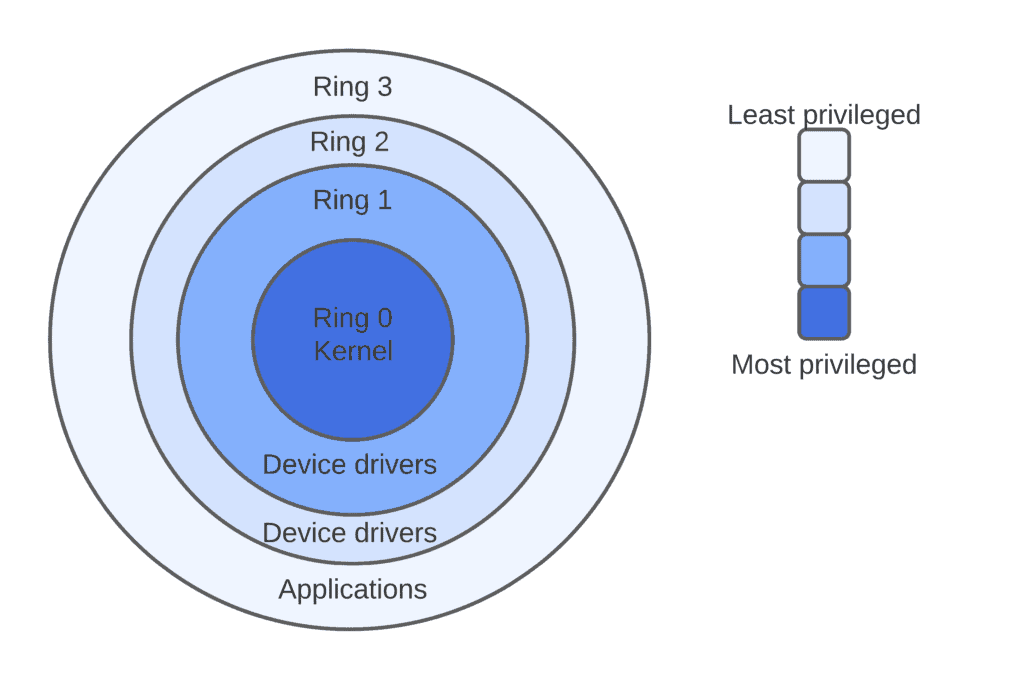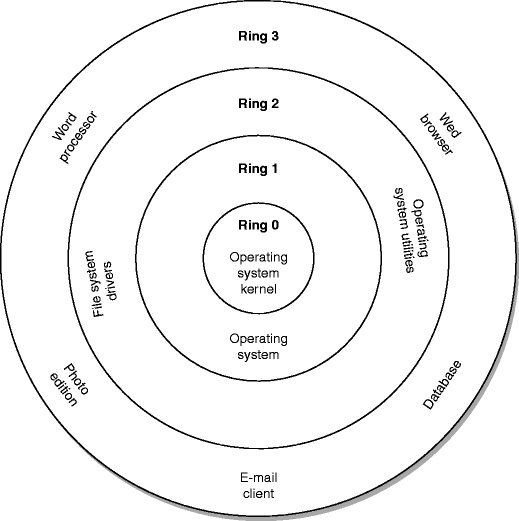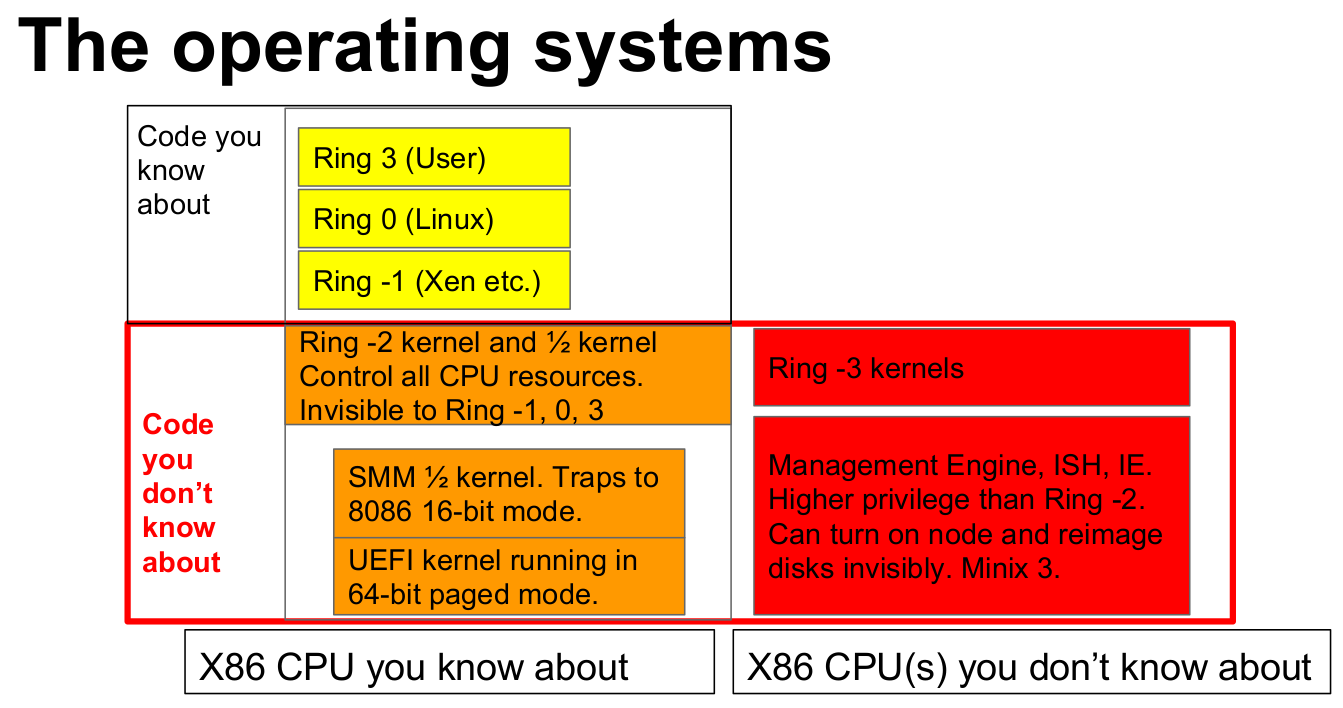
MINIX based Intel Management Engine Firmware & UEFI are Closed Source & Insecure, NERF to the Rescue! - CNX Software

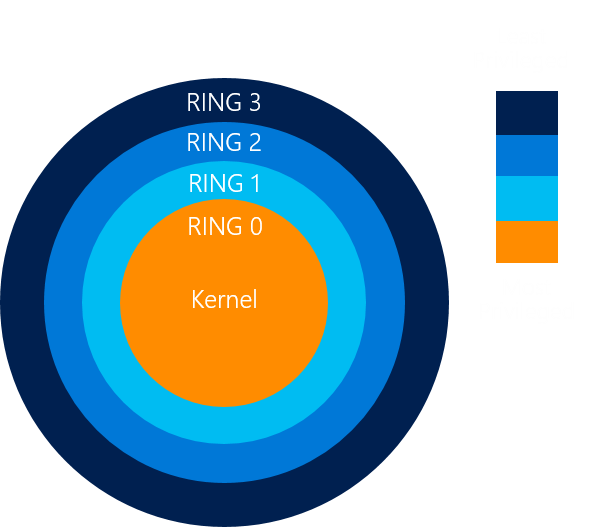
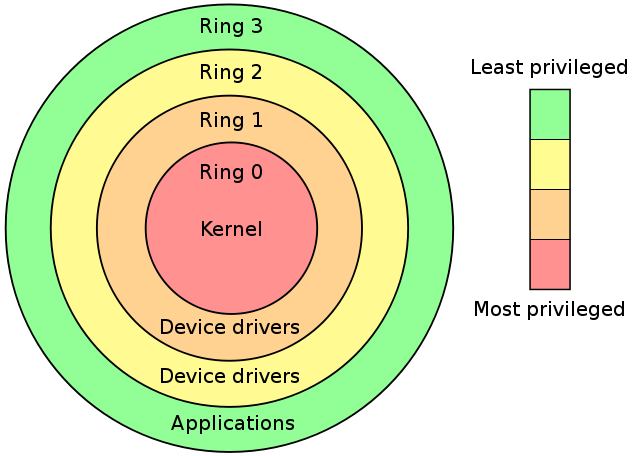
Hyper-V: Understanding and comparing the v1.0 and v2.0 architecture - TechNet Articles - United States (English) - TechNet Wiki

Amazon.com: FERRODAY 1/2 NPT Stainless Steel Thermometer Dial Thermometer 1/ 2 NPT Homebrew Kettle Thermometer Weldless with Lock Nut & O-Ring 0-220ºF Kettle Thermometer 3" Stainless Brewing Stock Pot Thermometer : Home &
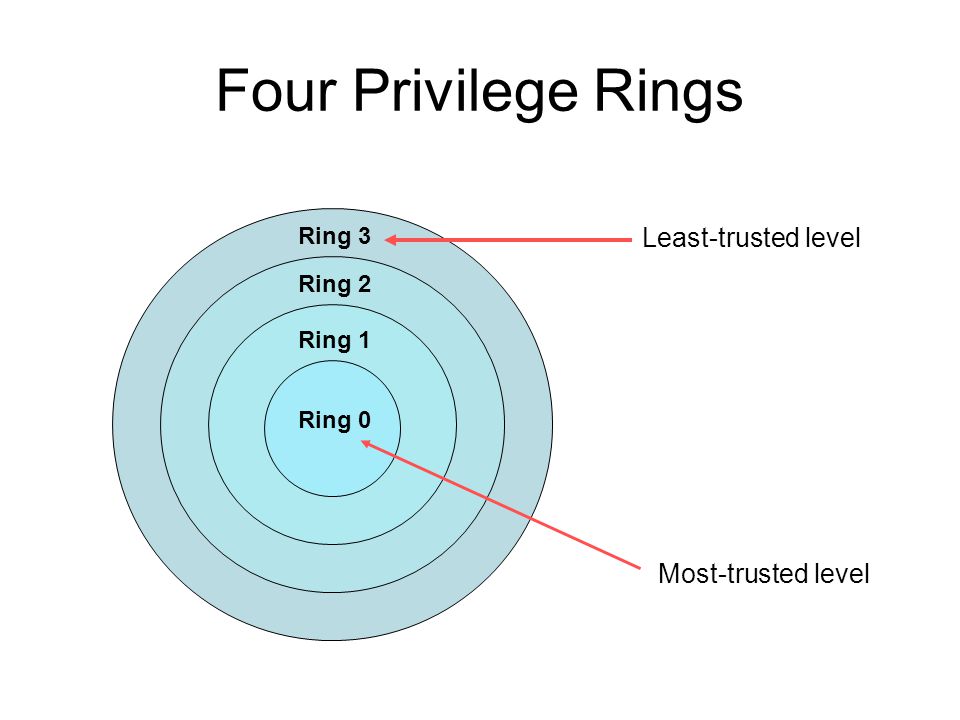
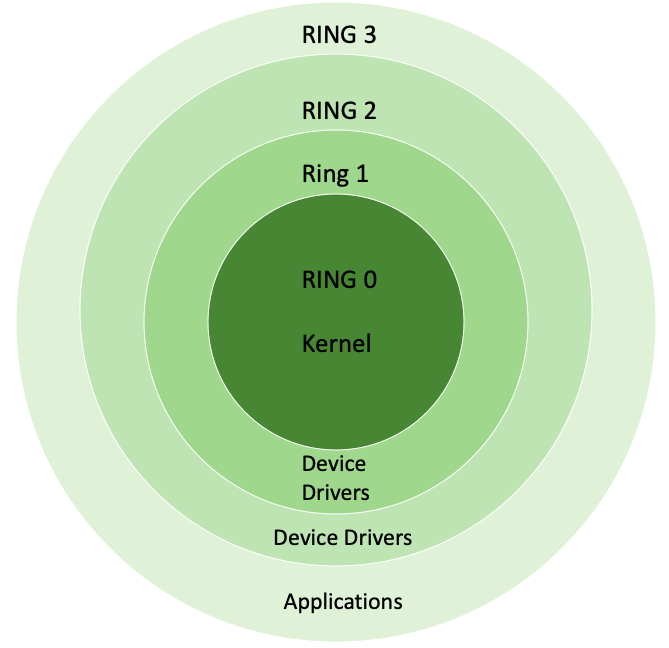
Processor Privilege-Levels How the x86 processor accomplishes transitions among its four distinct privilege-levels. - ppt download